For SMEs or whatever the use case it may not be applicable to rely on azure AD for your banned password implementation to conform with the new NCSC baselines and NIST recommendations of a banned password list.
Well good news there’s an password filter .dll implementation that does exactly what you are looking for which can be downloaded from here
There is also instructions on the main page of the github project however there is also instructions for the installation and some easy follow screenshots for guidance below.
First you need to get a list of banned passwords that you do not want to be used in your infrastructure. I have a list of ~29 Million here Or there are various other resources such as those stored on SecLists save this list as PassFiltExBlacklist.txt and overwrite the default.
You should then move the PassFiltEx.dll into the C:\Windows\System32 (or %SystemRoot%\System32) directory. along with the PassFiltExBlacklist.txt file which you edited with a list of passwords to be banned in your infrastructure. (the list in the screenshot is empty so ignore the size)
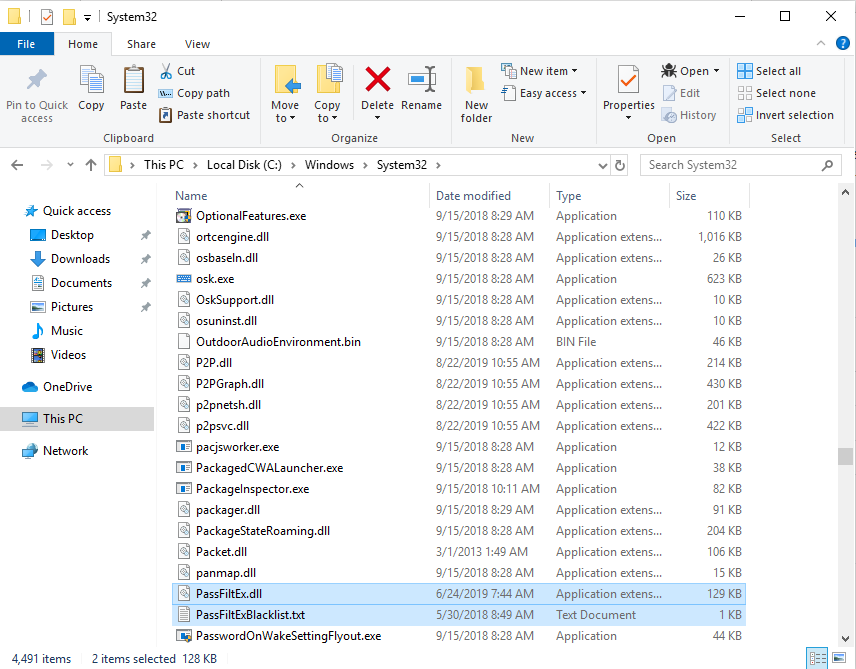
Once this is done open regedit (open powershell and type regedit and accept the UAC prompt) From here navigate to
HKLM\SYSTEM\CurrentControlSet\Control\Lsa => Notification Packages

Once open Notification Packages and append the file by adding PassFiltEx to the data as seen below

Afterwards just reboot the controller and that’s it! Naturally you will need to repeat the process on every domain controller.
For more information of password filters see here
A brief explanation is that when an administrator or user attempts to set a password it will be checked against all the password filters. Now this additional password filter is configured a password that fails to pass this filter will not be set and a user will receive an error.
